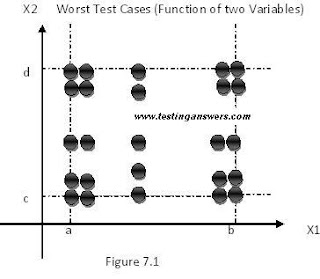
7.0 Worst-Case Testing
Boundary Value analysis uses the critical fault assumption and therefore only tests for a single variable at a time assuming its extreme values. By disregarding this assumption we are able to test the outcome if more than one variable were to assume its extreme value. In an electronic circuit this is called Worst Case Analysis. In Worst-Case testing we use this idea to create test cases.
To generate test cases we take the original 5-tuple set (min, min+, nom, max-, max) and perform the Cartesian product of these values. The end product is a much larger set of results than we have seen before.
We can see from the results in figures 7.1 that worst case testing is a more comprehensive testing technique. This can be shown by the fact that standard Boundary Value Analysis test cases are a proper subset of Worst-Case test cases.
These test cases although more comprehensive in their coverage, constitute much more endeavour. To compare we can see that Boundary Value Analysis results in 4n + 1 test case where Worst-Case testing results in 5n test cases. As each variable has to assume each of its variables for each permutation (the Cartesian product) we have 5 to the n test cases.
For this reason Worst-Case testing is generally used for situations that require a higher degree of testing (where failure of the program would be very costly)with less regard for the time and effort required as for many situations this can be too expensive to justify.
7.1 Robust Worst-Case Testing
If the function under test were to be of the greatest importance we could use a method named Robust Worst-Case testing which as the name suggests draws it attributes from Robust and Worst-Case testing.
Test cases are constructed by taking the Cartesian product of the 7-tuple set defined in the Robustness testing chapter. Obviously this results in the largest set of test results we have seen so far and requires the most effort to produce.We can see that the function f (to calculate the number of test cases required) can be adapted to calculate the amount of Robust Worst-Case test cases. As there are now 7 values each variable can assume we find the function f to be:
f = 7n
This function has also been reached in the paper A Testing and analysis tool for Certain 3-Variable functions [2].
The results for the continuing example can be seen in figures 7.2